A simple way to get around Websense and other web security software
Posted
Thursday, August 25, 2011 3:43 PM
by
CoreyRoth
A lot of companies out there are terrified by things like Facebook, Twitter, and even free web mail accounts. They end up running out and buying the first web security product they can find such as Websense. Out of the box, these products do an ok job at blocking most user requests to those “bad websites”. However, one day I noticed something about these products. They are easy to get around. Ridiculously easy to get around. One day I brought my laptop to the client site. I was working on it the previous night and I left the browser open with a few tabs open to Facebook and my Gmail account. I was used to these sites being blocked at the client, however, I noticed that the content wasn’t blocked this time. I was freely able to update my Facebook status and check my e-mail. I thought this was odd, so I tried the sites on another machine and I got the standard block message, like the one below.
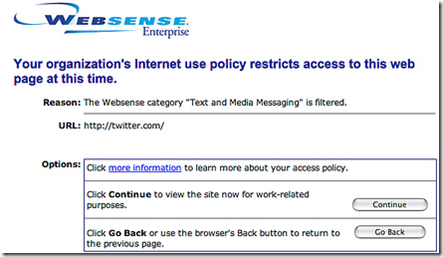
It took me a second, but then I finally noticed the difference. On the other machine, I had just typed in twitter.com and it was blocked. I went back and looked at my laptop and noticed it was point to https://www.twitter.com. I then tried several other sites. As soon as I used https instead of http, sure enough, the request when right through. Now, this only works on web sites that have SSL certificates, but a lot of the sites that are blocked usually support SSL. If you are interested in twitter specifically, I have often found that the web site is blocked, but using the API is not. That means you can run TweetDeck or your favorite Twitter client and it will probably work.
It’s as simple as that. Now, what you are doing is basically knowingly violating your company’s network security policy. So don’t go blaming me if they catch you and fire you for going somewhere that you shouldn’t. If you do get caught, I suppose you can always play dumb, and say “It wasn’t blocked so I thought it was ok now.”
Now, I’m not a network administrator by any means. I’ve configured a firewall and router or two, but that’s definitely not my expertise. I asked a buddy who was a network architect, why do so many companies let https traffic go through if they are concerned about content filtering. There were a few possible answers he gave. The first being that the companies don’t know that https traffic goes right through the web security product. The second answer was that they did know and they were just being lazy. After all they claim the average user wouldn’t know to try https. Whatever the reason, I have yet to find a company with a web security product where this did not work. Admittedly, that’s not a a lot of companies in the scheme of things, but it is worth giving a try.
Now for all of you conservative CIOs out there that happened to have stumbled on this article and are sounding the alarms to your network admins, maybe you need to ask yourself why you are blocking these sites. If the answer is because you are afraid of lost productivity, someone probably needs to relieve you of your job. If your employees want to find ways to not be productive, they are going to regardless of what sites you block. When a user gets a site blocked error message like the one above, what are they going to do? Ten years ago, they would have waited until they got home to go visit that web site. Today, that employee is going to reach for his or her smart phone and post their latest status update there. In effect, you have actually caused your employee to be even less productive. Instead of typing in that status update from the keyboard, he or she now had to tap it in on a tiny virtual keyboard with the auto-correct messing up every other word. Think about that.